Cloud Services Things To Know Before You Get This
The hardware and also the software application parts of cloud computer allow the smooth implementation of cloud computing models in any kind of company. Cloud computer is smooth as well as attends to hassle-free job regardless of the medium of public, personal, or crossbreed cloud. This is thought about to be among the popular solutions provided by cloud vendors.
The code maintainability in cloud computer is pretty high, allowing organization-wide coordination. It depends upon the search, reuse, and also modification of various other team codes and also enhances precision in the process of cloud computer. For that reason, cloud computing is simple to preserve thinking about the present scenario by generating a huge codebase for massive organizations.
Some Ideas on Cloud Services You Should Know
The cloud computer system is very easy to accessibility to take care of the information. It assists to gain access to online information quickly the organizations. It is simple to build and is immune to any kind of sort of mistake resistance. The developers can add extra sources to designate them from a redundancy of any kind of kind.
Cloud computer will aid the group members to function with each other irrespective of their area. Cloud companies usually come up with a cloud solution design called Software application as a Solution or Saa, S.
Not known Details About Cloud Services
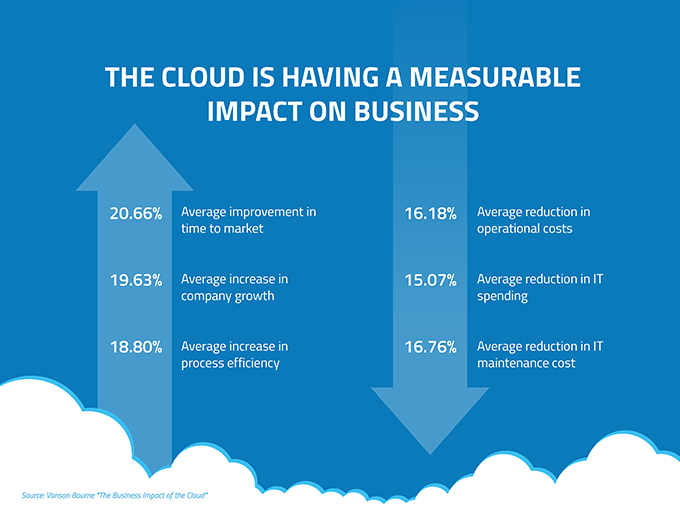
Cloud computing procedures mainly focus on these aspects and, thereby are thus primarily on mainly storage and respecting as well as appreciating. Cloud computing can examine huge data in cloud systems which creates a competitive advantage in the world of cloud service.
The speed and agility of cloud computing are what sets it class apart. To recognize what is the need for cloud computing, do take a look at the Knowledge, Hut website for its spotless Knowledge, Hut Cloud Computing online training. Cloud computing is really vital in today's time. It helps people to get knowledge regarding how information can be kept even without the visibility of hardware (cloud services).
A hybrid cloud computer program is extremely common, which depends totally on a solitary cloud service for whatever. Individuals functioning as a developer in cloud computing have actually been paid exceptionally. Cloud computing work are among the highest possible paying tasks, which aid in giving you a profitable job choice.
Some Ideas on Cloud Services You Should Know
We become aware of cloud calculating regularly, but just what does it mean? The National Institute of Requirements and also Innovation (NIST) describes the essentials of cloud computing in this manner: Cloud computer is a version for allowing ubiquitous, convenient, on-demand network accessibility to a shared swimming pool of configurable computing sources (e.
In other words, cloud computer is an on-demand, utility-based design of computing. Customers can access computing solutions using the cloud when they need to without communication from the service company. Cloud application solutions are the most well-known of the cloud service models.
What Does Cloud Services Mean?
This is where all the solutions and supporting framework are managed off-site over the Net and shared across numerous customers (or best site occupants). A fine example of a public cloud at the private customer level is a streaming service like Netflix or Hulu. Individuals register for the service with try this website a specific account yet access the very same services across the system through the Internet.
Public clouds are typically less costly than private as well as hybrid cloud solutions (in addition to traditional on-premise computer) because they count on economies of range. Users do not need to spend for solutions they aren't using and don't need to stress over handling and also maintaining the physical framework. An exclusive cloud gives IT solutions through the Internet or a personal network to pick customers, as opposed to to the general public.

This is a preferred choice for lots of organizations who want the agility of the cloud with better modification as well as security. Exclusive clouds can stay on-site or off-site.
An Unbiased View of Cloud Services
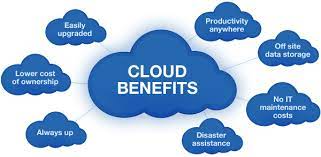
By handling your data and software program on the cloud, staff members can access needed details as well as interact with each various other whenever and any place they desire from their laptop computer, smart device, or various other Internet-connected gadgets. Cloud-based remedies open opportunities for farther work as well as higher productivity as well as effectiveness as everybody is guaranteed access to the very same upgraded info at the touch of a button.
Cloud computer is not just a trendy application that individuals can utilize to keep their photos and also videos online. It belongs to a business model that is taking the globe by storm. Cloud computing not just transforms just how a lot of businesses store and access data, however check my source it is also altering the amount of of these companies run.